Troubleshooting Windows Azure Pack Console Connect
What is WAP Console Connect?
WAP Remote Console Connect allows tenants to connect to their virtuals machine through a SSL-tunnelled RDP connection regardless of the virtual machine having an IP address or Remote Desktop connectivity enabled. The good thing here, it also works for Linux based VMs in the same way. The “bad” thing, the connection, even when RDP based, doesn’t allow client interactions like clip board, local drives, smart cards, etc. I’m not sure if this is be design for security reasons. However, when connecting via Internet, a dedicated Remote Desktop Gateway is required, as the RD Gateway gets a special “claim based authentication”-configuration making it unusable for other purposes like Remote Desktop Sessions or Remote Apps.
This post’s intend is to highlight the most common mistakes when implementing Windows Azure Pack Console Connect feature.
I’m not going in detail through the installation and configuration procedure, as this is documented in this TechNet Article.
To give you a basic understanding, I pasted the original Microsoft big picture here.
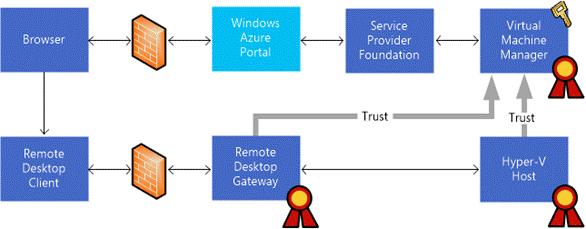
Image: Remote Console Connect Architecture (Image Source: Microsoft)
How it works “in a nutshell”
While it is a bit more complex in detail, I tried to simplify the process for a short overview.
- User connects to Tenant Portal and selects a virtual machine to connect to its remote console (not RDP)
- Azure Pack connects via Service Provider Foundation to SCVMM and asks for an access token
- SCVMM knows the Hyper-V Host, the VM is currently running on and creates a claim token using the private key of the installed VMM Gateway Certificate
- The token together with a dynamic issued RDP file are returned to Azure Pack Tenant Portal and user is asked if he wants to open the signed RDP file
- RDP Connection is established via RD Gateway to the Hyper-V Host, the VM currently runs on
- The Hyper-V Host verifies the claim token using the public key of the VMM Gateway Certificate and grants access to the VM Remote Console
These are the basic requirements to get this thing up and running.
- A valid SSL Certificate on SCVMM host with “Client Authentication” as enhanced key usage. If as self-signed certificate is used, it must also to be present on each Hyper-V Host (Local Machine Cert Store)
- A valid SSL Certificate on the RD Gateway host with “Server Authentication” as enhanced key usage
- Remote Console Connect configuration on SCVMM host
- Federated Authentication Gateway component installed on the RD Gateway
- Trusted certificate thumbprint set for RDP file signing on RD Gateway (the thumbprint of the certificate from Step 1)
- RDP Client 8.1 on the endpoint. See here for a Windows 7 version of RDP 8.1 Client
Most common deployment mistakes
Mistake 1:
- A self-signed SSL certificate has been used on SCVMM to generate the access tokens, but the certificate has not been imported into the computers certificate store on each Hyper-V Host
- A self-signed SSL certificate has been used on SCVMM to generate the access tokens, but the certificate’s public key has not been imported in the “Trusted Root Certificate Authorities” container on each Hyper-V Host
**In both cases above, Your browser will get a JSON file containing a not very helpful error message, instead of receiving an RDP File when trying to connect a VM Console
**
Mistake 2:
- The certificate has been issued with an invalid cryptographic service provider type -> “Microsoft Enhanced RSA and AES Cryptographic Provider” is required.
In this case the VMM Logs will display the following error:
SCVMM Version=3.2.7620.0
SCVMM flavor=C-buddy-RTL-AMD64
Default Assembly Version=3.2.7620.0
Executable Name=vmmservice.exe
Executable Version=3.2.7510.0
Base Exception Target Site=140727707248024
Base Exception Assembly name=mscorlib.dll
Base Exception Method Name=System.Security.Cryptography.CryptographicException.ThrowCryptographicException
Exception Message=Invalid algorithm specified.
Mistake 3:
- The thumbprint of the SSL certificate installed on SCVMM has not been registered on the RD Gateway host
- The SSL Certificate for RD Gateway Host has been changed or renewed without restarting the host
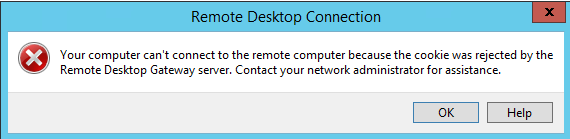
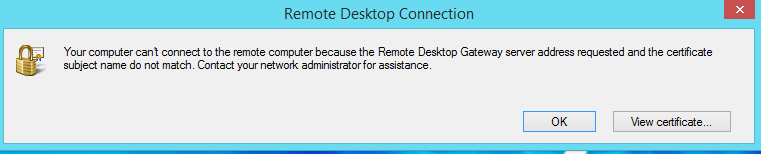
Mistake 4:
- The RD Gateway URL defined on the VM Cloud in WAP Portal does not match the CN of the RD Gateway Certficate.
- The Certificate used for RD Gateway does not have DNS=
set as a “Subject Alternative Name” - In this case you’ll see the following error message:
While there are other pitfalls like SSL-Offloading, Load-Balancing etc., I hope this post covers the most often occurring issues and questions I see around Windows Azure Pack Console Connect feature. However, if you know other important pitfalls, feel free to ping me: @DRMIRU